The steps should be used as a backup solution, in the case that the extend schema action from the eSSO Logon Manager Administrative Console fails. Also, if there is a problem using the LM Administrative Console this procedure can be used for gathering more information about the actual failure in schema extension.
To manually extend the Active Directory schema one must have eSSO Administrative Console installed, either locally on the Active Directory server or remotely.
Copy the following two files from the Administrative Console install to the Active Directory server:
C:\Program Files\Passlogix\v-GO SSO Administrative Console\DirectorySchema\vgo\AD
AttrTypesAD.txt and ObjClassAD.txt
Edit the two files and replace all occurrences of:
My Environment is – “nvdevserver.identity.us.com”
DC=identity,DC=us,DC=com
with the AD domain name, for example:
DC=identity,DC=us,DC=com
> ldifde -j C:\ -i -f c:\AttrTypesAD.txt
> ldifde -j C:\ -i -f c:\ObjClassAD.txt
Check the log files created for any Active Directory errors. The log file will be created in the folder mentioned by -j switch of the above commands.
How to Confirm Schema Extensions in Active Directory for an eSSO Repository
Here are the steps to follow for schema extensions in AD as an eSSO repository:
To confirm that the schema has been properly extended, use the following steps:
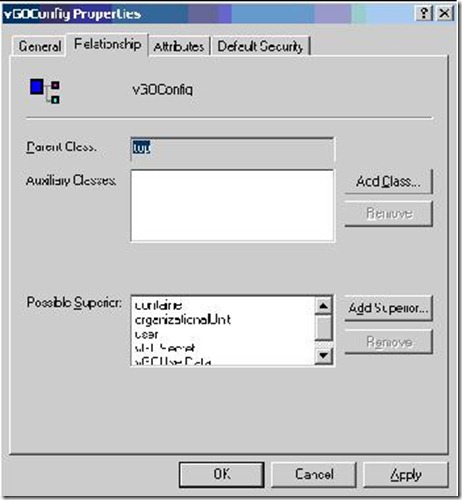
1) Using the Active Directory Schema MMC snap-in, open Classes and confirm that the following four classes exist: vGOConfig, vGoLocatorClass, vGOSecret, vGOUserData.

Right-click vGOUserData, choose Relationship tab, confirm User is a possible superior. 
Right-click vGOUserData, choose Relationship tab, confirm User and Container are possible superiors
To confirm that proper rights have successfully been assigned when storing v-GO user secrets under Active Directory User Objects, use the following steps:
Using the ADSIEdit MMC snapin, browse to the root of the tree, right-click and choose properties. In the “Advanced Security…” dialog, click on the advanced button and browse to the bottom of the list, where two entries should exist of Name “SELF”.
Highlight the first entry and click the Edit button.
In the “Permission Entry…” dialog, with the Properties tab selected, browse to the bottom of the list and confirm the Create vGOUserData Objects and Delete
vGOUserData Objects exist and are checked to Allow.
Repeat the above steps, except this time examine the properties of an individual user object in the tree to make sure the rights inherit all the way to the user object. Oracle eSSO assumes that rights inheritance is not blocked between the root of the tree and the user object.