Installing SSPR 5.01 or 6 or 7.0.1 in Active Directory (Windows Server 2003)
i. System Platform Requirements: For the purposes of this document, it is assumed that Windows 2003 Server is being
used as the chosen server operating system. The following are required components:
- .Net framework version 1.1 or higher (version 2.0 recommended)
- Windows Server 2003 Service Pack 1 or higher
- IIS Server installed with ASP.Net installed
- The latest Microsoft Windows Updates (recommended)
step by step installation and configuration of Passlogix’s Self-Service Password Reset product (hereinafter “SSPR”) for both server and client-side components with enhanced security settings.
Following things to be taken care by System Administrator
Avoid installing the
SSPR Server-Side components on a Domain Controller, use a member server.Ensure that DNS is configured and working properly including correct enumeration of forward and reverse lookup zones.
Ensure that both servers and workstations have the latest service packs and windows updates installed on them.
For the creation of service accounts, consider long complex passwords and set the accounts to lock out after a finite set of bad password attempts – this will prevent a hacker from attempting a dictionary attack on service accounts.
Installing SSPR in Active Directory (Windows Server 2003)
Part A – Account Creation
On your domain controller, create the following accounts making them ordinary users in the domain users group (default):
SSPRWEB: This account will be responsible for SSPR IIS functions and will make changes, additions, etc., to the Organizational Unit that will be created in a later section of this document.
SSPRRESET: This will be the account that will be running the actual service on the SSPR member server with IIS and will be responsible for resetting user passwords on the domain level
Part B – Server Installation
we have already discussed that we do not recommend installing the SSPR server-side components on a Domain Controller.
Log onto the IIS Member Server where you have local administrative rights – log into the domain, not the local machine. (Here i used XP Machine and that is the member of Domain Controller Machine)
Locate the executable for the SSPR server-side component and install it selecting the defaults and performing a full installation. The default language is English and you can choose the desired language during this initial installation.
Part C - Assigning the Password Reset and Web Service Accounts
i. From the Services Icon on the member server that you installed the DPRA serverside components on located in Start/Settings/Control Panel/Administrative Tools/Services, locate the Self Service Password Reset service. Right click it, click Properties, then click the Log On tab and assign the SSPRRESET Log on as rights to the Self-Service Password Reset service.
Installing SSPR in Active Directory (Windows Server 2003).
Restart the service as indicated.
On the IIS Member Server where you installed the SSPR server-side components open the IIS Manager from the Administrative Tools program folder and navigate down to the default website. Locate the vgoSelfServiceReset virtual directory, right click it, select the Directory Security tab. Under Authentication and access control, click edit.
When the Authentication Methods dialogue box appears, enter the name of the SSPRWEB account in the Use the following Windows user account for anonymous access box as well as its password. Confirm the password.
Click START, then RUN and type iisreset – this will restart IIS.
If you still have the IIS console open and attempt to browse an item therein, you will receive an error message about needing to reconnect. If you are prompted, answer yes. This is because the IIS service was restarted.
IMPORTANT PONITS TO BE REMEMBERED
Virtual Directory: vgoSelfServiceReset
Enable Anonymous Access = YES
Integrated Windows Authentication = YES
Authentication and Access Control Account = DPRASERVICE
Virtual Directory: EnrollmentClient
Enable Anonymous Access = NO
Integrated Windows Authentication = YES
Authentication and Access Control Account = DPRASERVICE
Virtual Directory: ManagementClient
Enable Anonymous Access = NO
Integrated Windows Authentication = YES
Authentication and Access Control Account = DPRASERVICE
Virtual Directory: ResetClient
Enable Anonymous Access = YES
Integrated Windows Authentication = YES
Authentication and Access Control Account = DPRASERVICE
Virtual Directory: WebServices
Enable Anonymous Access = YES
Integrated Windows Authentication = YES
Authentication and Access Control Account = DPRASERVICE
The only two virtual directories that do NOT permit anonymous access are EnrollmentClient and ManagementClient.
Part D – Granting Registry Access to the Web Service Account
In order for SSPR to function properly, grant the SSPRWEB service account full permissions to the following registry key on the member server where you are installing the SSPR server side components.
HKLM\SOFTWARE\PASSLOGIX
Part E – Temporarily Make both the Password Reset and the Web Service Accounts Members of the Local Administrator’s Group on the IIS Server.
To avoid possible permissions problems during the installation of the SSPR server side components, its recommended that both the SSPRWEB and SSPRRESET, accounts be made members of the local administrator’s group on the IIS Member Server you are installing the SSPR server-side components on.
Once you have finished the installation and configuration of the SSPR Server-Side components, you may remove these accounts from the members of the local administrator’s group on the member serverPart F – Verifying Proper Assignments of Web Service & Password Reset Accounts
To access the SSPR web-based console, open IIS and navigate down to the Default Website then to the vgoSelfServiceReset, ManagementClient. In the right pane, scroll down to the webservice.aspx page and browse to it:
In the v-GO SSPR Management Console web page, locate the System and Web Service Account section. Notice that the SSPRWEB account has already been assigned as the Current Account.
In the v-GO SSPR Management Console web page, locate the System and Reset Service buttons. Notice that the SSPRRESET account is listed as the service account for the Reset Service.
If the Password Reset Service is not listed as the account under the Reset Service Section of the SSPR Management Console web page, you should reset the IIS service using the iisreset command from the run line. If it does not appear, you can manually assign it by specifying the account with the following naming convention:
Domainname\SSPRRESET
If you receive an error message indicating that the account does not have log on rights to a service, make sure that the SSPRRESET and the SSPRWEB accounts are both members of the local administrator’s group on the IIS member server you are installing the SSPR server-side components on.
Click on Reset Service in the left pane and make sure that the SSPRRESET account is listed as the Reset Service Account.
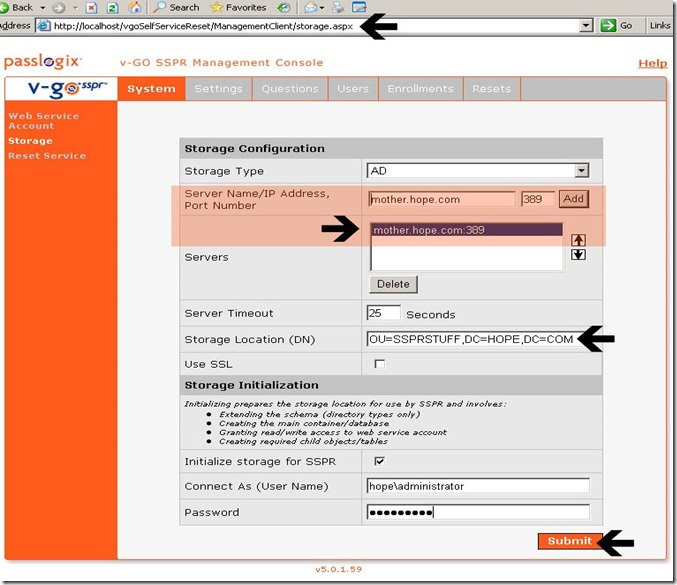
Notice that the SSPRRESET account has already been granted the role of Reset Service. Click on the STORAGE link in the left side of the page.
Part G – Enabling Storage in Active Directory
SSPR stores user questions, answers, configuration and enrollment information within an organizational unit in Active Directory. The name of this OU is your to choose.
As will be explained below, the “Connect as” account is the one that will actually be performing the schema extension, as such, this account needs to be a member of the Schema Administrator’s group.
It is important to note that if you do not connect to the server that holds the role of Schema Master2, you may receive an error message.
Select the storage type as AD, type the fully qualified domain name of the Domain Controller that holds the role of schema master3, type 3894 for the port number and click the ADD button. Next, populate the fields according to the following table.
Storage Type: For the purposes of this document, we choose AD
Server Name/IP Address, Port Number: Ideally, the fully qualified domain name of the Domain Controller where the SSPR OU will be created. The port number for AD is 389 – If you are using SSL, its port number 443.
Servers: This is where you can specify multiple servers. For the purposes of this installation, we are using a single domain controller.
Server Timeout: This value is set according to your needs. I used 25 seconds for reference, but you can change this value depending on the speed of your network in relation to AD replication.
Storage Location (DN): The information you enter here will determine the location of the DPRA OU that you create within Active Directory.
OU=SSPRSTUFF – This will be the name of the OU that is created
DC=identity – This is the netbios/short name of the domain
DC=com – this is the .com extension of the domainInitialize Storage for SSPR: Make sure that this box is checked. If you do not select this box, you will not be able to enter information into either the “connect as” or password fields.
Connect As: This is where you enter the name of the account which will actually extend the AD schema and create the SSPRSTUFF OU. As such, this account should be a domain administrator that has permissions to modify the schema. Please note, you should enter the username and password in this syntax –
Domainname/UsernamePassword: This is the password for the domain account that will actually be adding the SSPR organizational unit within AD.
click “submit”,
after slight delay and receive a “successfully saved changes” confirmation message
Note: To verify that this OU was created, open a fresh instance of Active Directory Users and Computers on your targeted domain controller. You should see an Organizational Unit named “SSPRSTUFF” (or the name that you chose) and two sub OU’s named SystemQuestions and Users, respectively.
You can now remove both the SSPRWEB and SSPRRESET accounts from the local administrator’s group on the IIS member server where you have installed the SSPR server-side components.Part H – Granting Permissions to the SSPRWEB Service in AD
After creating the OU and sub containers within Active Directory, we will grant limited, specific permissions to the Web Service account for the SSPR container we created in AD
Step by Step Instructions to Assign Advanced Permissions to the SSPRWEB service account to the SSPR organizational unit.
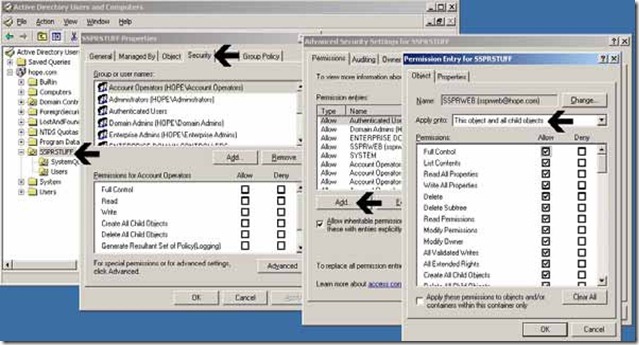
From Active Directory Users and Computers, make sure that you have selected Advanced Features from the View Menu.
From within Active Directory Users and Computers, right click the SSPR Organizational Unit, click the Security, click Advanced, click Add, type in the name of the SSPRWEB account and click OK. When the permissions entry tab appears, select FULL CONTROL and make sure that the Apply Onto section is set for “This object and all child objects”. Click OK and close all open windows. Check that the permissions have been set accordinglyOrganizational Unit SSPRWEB Web Service Rights
SSPRSTUFF Full Control
SSPRSTUFF/SystemQuestions Full Control
SSPRSTUFF/Users Full ControlRestart IIS with the iisreset command from the run line
Part I – Delegating Permissions to the Password Reset Service Account
In order to reset the passwords of users who are enrolled in SSPR, the Password Reset Service account needs limited rights – specifically, resetting passwords and nothing more.
1. Consider granting the password reset account granular permissions based on Organizational Units. If your users are divided into OUs, this matter will be simplified.
2. Consider granting the password reset account permission to specific groups within AD: This will require you to manually grant the password reset account permissions to specific groups which will be explained below
Do NOT run the delegation of control wizard at the root of your domain: If you do so, the password reset account will have this right not only for users, but will flown down to objects such as computers, printers, etc.
As a final, important note: Since the password reset account is a member of the domain users group, granting it password reset permissions is applied to users at the same level.
For example, if you store all of your users in the default users container in AD and run the delegation of control wizard at this level, it will NOT apply to members of your administrator’s group – this occurs by design in Active Directory.
In the scenario above, the password reset service account will NOT be granted permission to reset the password of your administrators. Your administrators will be able to enroll in SSPR and even go through the entire password reset dialogue, but the moment they attempt to reset their password they will receive an error message.
This is because the password reset service account does not have permissions to reset the password for such users.
Granting the Password Reset Account Permissions at the Group Level
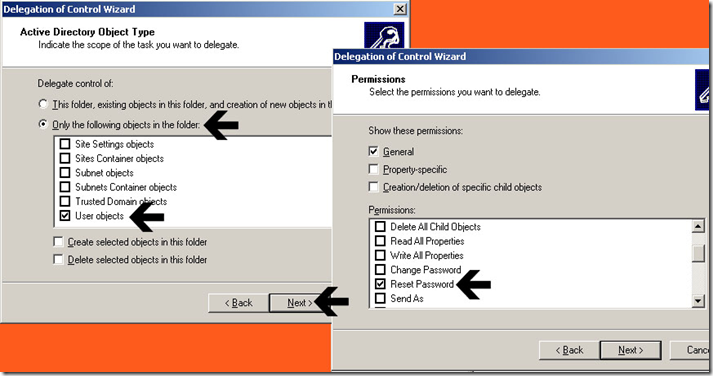
If you have not separated users into Organizational Units as discussed above you can never the less manually assign advanced security for the Password Reset Account to specific groups and even specific users – The delegation of control wizard is NOT available at the user or group level.
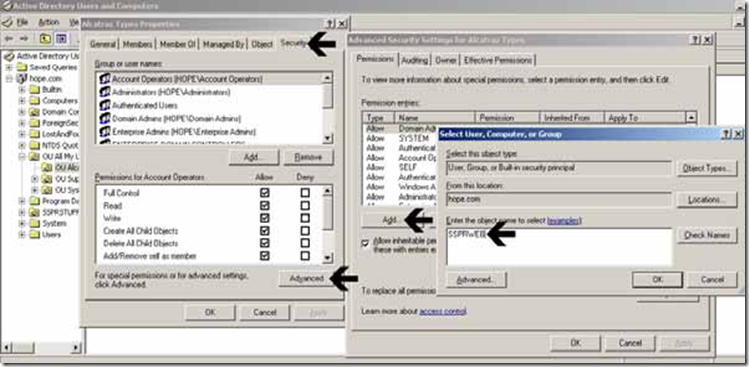
To manually assign the SSPRRESET account permission to reset user passwords for users or groups, right click the Group or User object and select the security tab, click Advanced, then click ADD and insert the name of the Password Reset service account – click OK.
When you click OK you will be presented with a permissions entry window. From the “apply onto” drop down box, select User Objects and scroll down to the Reset Password checkbox.
Click OK and Apply as indicated. If you want to ensure that permissions have been applied, view the security tab of the group or user object to confirm that permissions have been applied accordingly.