Passlogix v-GO Provisioning Manager provides the ability for an administrator to automatically provision v-GO SSO with a user’s ID and password by using a provisioning system.
An administrator is able to add, modify and delete IDs and passwords for particular applications within the provisioning system and have the changes reflected in v-GO SSO. From the provisioning system, all usernames and passwords inside of SSO can also be deleted so that a user’s access to all protected applications is eliminated.
Installation Overview
Provisioning Manager is installed as an add-on component to v-GO SSO. SSO must be installed prior to installing Provisioning Manager.
System Requirements and Supported Applications
In order for Provisioning Manager to install and function properly, your system must meet at least the following requirements.
Pentium III class processor at 900MHZh
512MB RAM
Disk Space: a complete Installation requires ~3MB
Provisioning Manager Support for SSO Agent needs < 1 MB of additional disk space
Software Requirements
In order for Provisioning Manager to install and function properly, your system must have the following applications installed:
Internet Explorer 6.0 or higher with 128-bit encryption
Microsoft® .NET Framework 1.1 (installed by Provisioning Manager installer)
Microsoft Web Services Enhancements (WSE) 2.0 SP3 for Microsoft .NET (installed by Provisioning Manager installer)
Provisioning Manager Support for SSO Agent
In order for the Provisioning Manager support for the SSO Agent to function properly, v-GO SSO must be installed.
Provisioning Manager Server
In order for Provisioning Manager Server to function properly, your system have the following applications installed:
- Microsoft Windows® 2000 Server, or Windows Server 2003
- Microsoft Internet Information Server 5.x or 6.x (6.x recommended)
- Microsoft Active Directory®, Microsoft ADAM, Sun Java System Directory, or IBM LDAP Directory
Microsoft SQL Server 2000 or Microsoft SQL Server 2000 Desktop Engine (MSDE 2000) (only required if using Event Logging)
IIS Requirements:
Microsoft Internet Information Server (IIS), version 5.0 or later. Provisioning Manager uses the IIS Web server to provide a browser-based interface for user enrollment, general setup and administrative tasks.
Note: If Active Directory or ADAM is used, the IIS account must have Administrative privileges and must be in the same domain.
Provisioning Manager Repository Requirements:
Provisioning Manager can use any the following as the repository:
Microsoft Active Directory or Active Directory Application Mode (ADAM). The Active Directory server or ADAM instance (that is, Active Directory running as a user service) can be on any server and in the same domain.
Sun Java System Directory
IBM LDAP Directory
Installer Requirements
To install Provisioning Manager, you need to have Administrative privileges for the PM/IIS server. You need to provide the following information to configure a Directory server:
| localhost | Host name of the server for Directory server instance. |
| port | Port number of Directory server instance. |
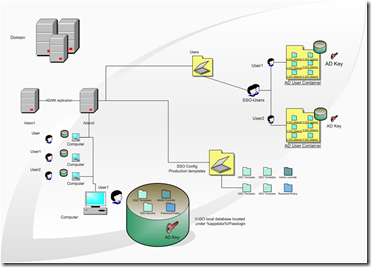
In my Virtual Machine environment i will use two servers (SSOLABDC, SSOLABMEM) and one client machine (CLIENT).
- SSOLABDC
- Domain controller for SSOLAB Domain acting as repository for SSO Configuration
- Enterprise Root Certificate Authority
-
- SSOLABMEM
- Member server in SSOLAB Domain
- IIS 6.0 Server
-
- CLIENT
- Member of SSOLAB Domain
- SSO Admin Console tasks performed from here
- SSO Agent installed
-
1.1 Installation of the Passlogix v-GO Provisioning Manager Server program files
1. On SSOLABMEM, click Start | Run, enter & click OK.
2. Navigate to the Passlogix\v-GO PM\Server folder.
3. Double-click the v-GO PM Server.exe file to begin the installation.
4. The Welcome Panel appears. Click Next.
The License Agreement panel appears. Read the license agreement carefully. Click the I accept the terms in the license agreement button and click Next to continue
The Setup Type Panel appears. Select Complete or Custom. Complete installs all program files. Custom allows you to choose what program files are installed and the location. Custom installations are only recommended for advanced users. Click Next
Provisioning Manager is ready to be installed. Click Install. Wait for the installation to complete. When it is done, click Finish.
Click on finish button
Create or identify a user account for anonymous login
A dedicated Anonymous User account through which Provisioning Manager users and administrators access Provisioning Manager Web Services must be created or identified. This Anonymous User account should be a member of the Administrators group.
Because the default Anonymous User account for a Web service, IUSR_<MACHINE_NAME>, is not a member of the Administrator group, you must create or choose a domain user account that is an Administrator; this will allow the account to perform these tasks
To create a new user account or assign Administrator rights to an existing account,
use the Active Directory Users and Computers ----------------console (for an Active Directory domain) or the Computer Management console (for non-AD domains).
The user account you create or choose is specified as the Anonymous User dialog of the Services tool during this step.
Click Start, point to Program Files, point to Administrative Tools, and click Internet Information Services.
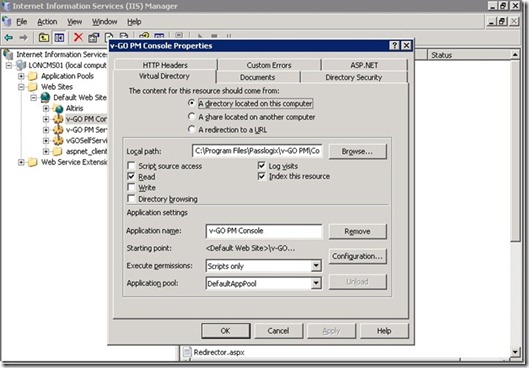
2. Locate the Provisioning Manager Console node in the tree, right-click on it, and click Properties.
Click the Directory Security tab and
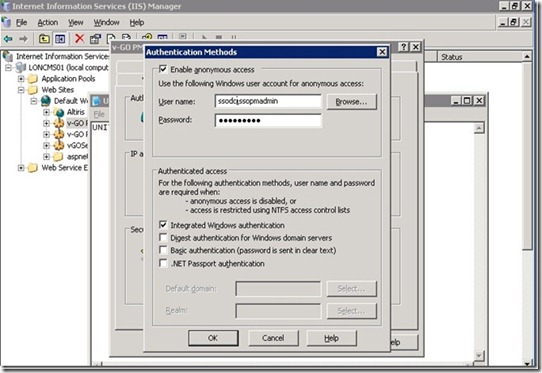
click the Edit button next to Anonymous Access
Check the Anonymous Access checkbox and type in the username and password of the anonymous user. The anonymous user must have local Administrative access.
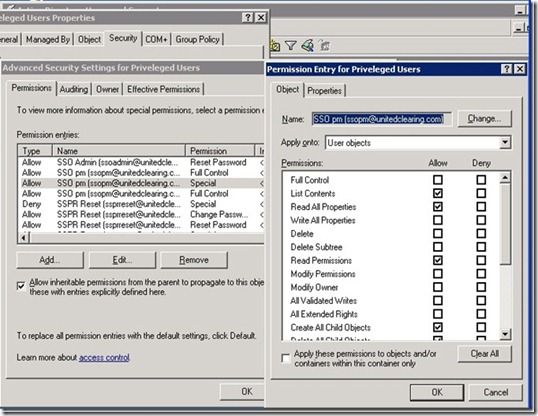
Granting Special Permissions within AD to the Provisoning Manager SERVICE Account here(SSOPM).
The next procedure is to grant special rights to specific containers within Active Directory to the PMSERVICE account. Remember that, to Active Directory, the PMSERVICE account is simply an ordinary user account.
To grant the special permissions:
1. In the Permission Entry for SSOConfig dialog box, grant the PMSERVICE account advanced full control of the SSOConfig container (the container where the application templates are stored) as shown in the following illustration:
Configuring the PM Server Settings
Access the PA Site by entering the following link on SSOLABMEM
http://localhost/v-GO%20PM%20Console/logon.aspx
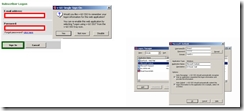
Enter SSOLABMEM/ssopmadmin for the Username and ********** for the Password and click Log On.
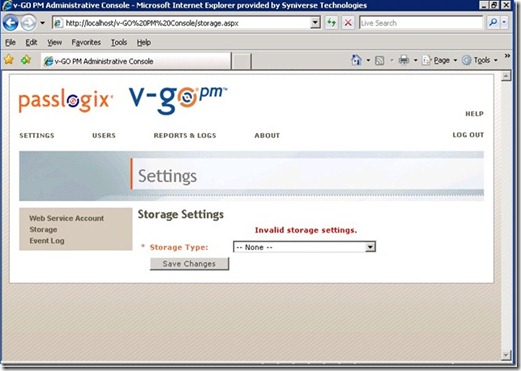
3. When logged in properly, you should see a screen like the one in the graphic below:
From the Settings page, click on Storage.
Select AD from the dropdown list and enter the settings displayed below to configure storage
Click Save Changes and this will return you to the login screen.
Log back into the Provisioning Manager program and click on Users. If you have properly configured the storage settings, you should see the following screen with all of the application templates you created in the SSO DC when you click on Users.




![clip_image001[5] clip_image001[5]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhyXXtutfiat_uSh78ZxDtrNnQPXZ4AQXgWNyj-jUEfFuNFHhJggGQ1YSlJVSVe6b1spik9y95fyPDBSHltUuIucNCLQRIys-y6msFyDRK2x63MIzYD48jOs-Lgy5KKUUpX1Qd_aFVk9-i2/?imgmax=800)
![clip_image002[6] clip_image002[6]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgVigOlJrK_5FFUbGl41X8fjFFYxQZLcv-D_62iUKUbiJ46Laq0AxgcLSsgjd-7G_zmAJWoRmnL8AG8QWzR1xD10Iusl7YiqK2g3L5-34Yux-i7zm1q5xZE2YcCWWULOWW4fhM4hq7HMokB/?imgmax=800)
![clip_image001[7] clip_image001[7]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEh_-uXmfUCvgY4Jlywbb1j1mpYpBHqP0UKQmdAe3iemecBnHpxbNptZYWThp957xEej4R6fAX7TkdRsRA3quDuRPaTc_QwsXus1Nc4Ngw9jR_sIbF0cnka0m7-MQP2SUDoN4mrwyD5hy0b7/?imgmax=800)
![clip_image002[8] clip_image002[8]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEib4s5WBWJi8h4w3PiewnM6PhKgQjRsqFSgboyTWoD56-yveRbu8CIJy23b-JscXzchCkdr_1N5_mIE6x4ZkIhBB2Sh2vrQIjeUmf9xPGHVHEaqDGNmMV94nqnWlRTEXGrQMRY8sePz2i8d/?imgmax=800)
![clip_image003[6] clip_image003[6]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjXTMChjpDyiW60hUyjP08nSGvD2zU73owOQrIjSwHZjylDKMlDCISQUY-9Q_rUIBbdCRIP2J_2WCOwlC6HglfbpheYwRcK9PKUbNttT78TGThX1qDrOnsQuvuFZkWtOnoZ-Fn3FidJ0VtX/?imgmax=800)
![clip_image004[5] clip_image004[5]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhMPwD8wKpKenTqCFfYzlR0c6Y9KffhYUbQLORXADQjgq01gz4nh4mqp1Vv0_FVPOroG3E_BiWPktF-hC7G_Rbcc3sAOD9gAOirAMhba5X_g0tnVoEGmFMDIyT4IJuQ4DMO-Tp8wDsrptv1/?imgmax=800)