ESSO-TEMPLATES for Different Applications.
eSSO Integration With Oracle Access Manager :
This note will describe the steps needed to create an application template for Oracle Access Manager default login page.
1. Open eSSO Administrative Console
2. Applications -> New Web App
3. Type in the name as "Oracle Access Manager"
4. In the address bar type the access login URL:
http://host:port/access/oblix/
5. Click on Policy Manager link
6. The page will load but will show "No forms found"
7. Click on "Go" button, in the upper right part of the window
8. Check "Show anchor tags"
9. Select the username, password and submit anchor and click Ok
10. The URL will be captured by the Administrative Console as a regular expression. We will need to edit the
URL to remove all dynamic content from it
+ click Edit
+ select Wildcard
+ type the value as
http://NXDEVSERVER:80/identity/oblix/apps/userservcenter/bin/userservcenter.cgi?program=commonLogin*
eSSO Integration With Oracle SSO
This note will describe the steps needed to create an application template for Oracle Single Sign On login page.
To define the template for this application, perform the following steps:
1. Open eSSO Administrative Console
2. Applications -> New Web App
3. Type in the name as "Oracle Single Sign On"
4. In the address bar type the OIDDAS URL:
http://NXDEVSERVER.IDENTITY.US.COM:7777/oiddas
5. Click on Logon link
6. Make sure both:
+Use ordinals instead of names
+Show anchor tags
are unchecked.
7. Click Detect Fields and make sure the fields are detected correctly
8. The URL will be captured by the Administrative Console as a regular expression. We will need to edit the
URL to remove all dynamic content from it:
+ click Edit
+ select Wildcard
+ type the value as http://NXDEVSERVER.IDENTITY.US.COM:7777/sso/jsp/login.jsp*
Oracle Forms Integration ESSO
integration of Oracle Forms based applications with eSSO product
1. Define a template using Control IDs and the Java Helper Object
2. Define a template using Send-Keys technology
Oracle Support recommends implementing the template using the first option.
There are several advantages for this:
+ by using the Java Helper Object the LM agent will be able to detect the
inner Logon window, instead of the applet window
+ credentials will be injected directly in the controls
+ the focus will be handled by the helper object
To implement the template, follow the steps bellow:
Java Helper Object setup
1. Determine the exact version of JInitiator used to run the Forms application
2. Download the following files:
ssojho.dll
jho.zip - rename to .jar
jaccess.zip- rename to .jar
accessibility.properties
Copy the files in the following locations:
Source file
Destination path
ssojho.dll C:\Program Files\Oracle\JInitiator 1.3.1.xx\bin
jho.jar C:\Program Files\Oracle\JInitiator 1.3.1.xx\lib\ext
jaccess.jar C:\Program Files\Oracle\JInitiator 1.3.1.xx\lib\ext
accessibility.properties C:\Program Files\Oracle\JInitiator 1.3.1.xx\lib
Note: this version of the JHO helper requires the Microsoft Visual C++ 2005 runtime to be installed on each machine where this is running. This can be downloaded from Microsoft website:
http://www.microsoft.com and search for Microsoft Visual C++ 2005 Redistributable Package (x86)Start the Forms application and the eSSO Administrative Console
5. In eSSO Administrative Console, select New -> Windows Application
6. Select the Applet window (module iexplore.exe, class SunAwtFrame), click next
7. If the helper object was installed correctly, at this point, the inner Login frame should be in the list
8. Select the login frame and continue the wizard by defining the credential fields
9. IMPORTANT: Once the wizard is finished, on the Miscellaneous tab of the login form definition, check "Preset Focus" Without this step the template will not work.___________________________________________________________________________
Create file with following Content and Save :”FormSample.ini”
___________________________________________________________________________**************************************************************************************
[FormsSample]
AllowClassName=JHOShadowWindow_Class
AppPathKey1=iexplore.exe
AppSubType=1
AT_AppGUID=dca0e7b2-c132-40d5-8468-b9a3db83e7ee
AT_PageGUID=4ff9538e-16ba-46ca-8c3e-8b682985e2dc
AT_PageName=FormsLogon
AuthGrade=1
IDCtrl=1:3:1:2,VTextField6,class oracle.forms.ui.VTextField,text
MaskThirdField=1
MatchType1=exact
OKCtrl=1:3:1:7:1,PushButton4,class oracle.ewt.button.PushButton,push button
OtherCtrl1=1:3:1:6,VTextField8,class oracle.forms.ui.VTextField,text
PassKeyCtrl=1:3:1:4,VTextField7,class oracle.forms.ui.VTextField,text
PresetFocusAll=1
UseJHO=1
WindowTitle1=Logon
Context=EO1Rvue73GsJHyASOFwXD5IFz37fC/3V+dKew5SUNKZspYiL[*Other Apps]
Section1=FormsSample
Context=sFMFy/Z3/RLLJpqpsgw/dL5pY4ex63oZpEmeoU2gGMjtYbKq
*****************************************************************************************Tuning the eSSO LM agent for Oracle Forms
Depending on the workstation and network performance, there are a few settings that can help. The following values are known to work in most cases, so it can serve as a starting point for your tuning effort.
Global Agent Settings
-> Live
-> Response
-> Java AppsDelay after Java runtime startup = 500ms
Delay between retries = 500ms
Maximum times to retry credential injection = 5
Time allowed for Java applets to load = 20 seconds
eSSO Defining Templates For Oracle Identity Manager
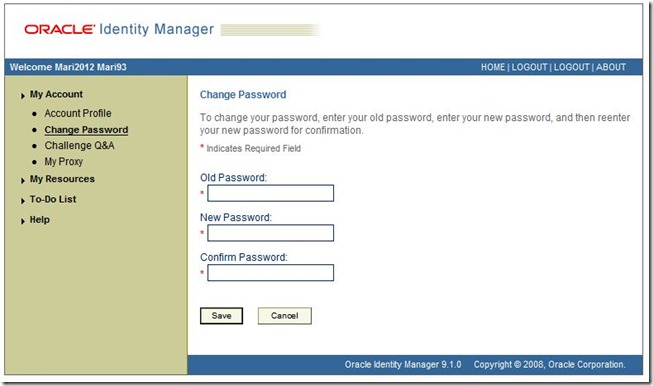
This document provides the procedure to create eSSO templates for Oracle Identity Manager web interface login and change password screens, and for Oracle Identity Manager Design Console login screen.
The OIM web interface change password screen is:
The OIM Design Console login screen is:
To define the template for the OIM web interface login screen:
1. Open eSSO Administrative Console
2. Select New-> Web Application
3. Enter the URL of your login screen: http://NXDEVSERVER.IDENTITY.US.COM:7001/xlWebApp
4. Detect the credential fields and the submit button
To define the form for the change password screen:5. Select the application template defined before
6. Right click and New Form
7. Navigate to the change password page using the wizard
8. Give a name to the Form and save the template
SAMPLE TEMPLATE___________________________________________________________________
[dc7bd56d-474c-45de-b0db-cedc5cb35853]
AT_PageGUID=dc7bd56d-474c-45de-b0db-cedc5cb35853
AT_PageName=OIM Web Interface
IDField=0,logonForm,username,text
ParentKey1=OIM Web Interface
PassField=0,logonForm,password,password
SubmitField=0,logonForm,3,submit
URL1=.*?http://localhost:8080/xlWebApp.*
URLMatchType1=regex
URLReferrer=http://localhost:8080/xlWebApp
Context=w+1GsHyqz7PsxRSEcmhliFomgVuUHZBB3eFe6Z+CBGY/jpAq[3711a0a2-89a1-47ee-9259-e30512f84515]
AT_PageGUID=3711a0a2-89a1-47ee-9259-e30512f84515
AT_PageName=Change Password
NewPWField=0,changePasswordForm,newPassword,password
NewPWField2=0,changePasswordForm,confirmPassword,password
ParentKey1=OIM Web Interface
PassField=0,changePasswordForm,oldPassword,password
SubmitField=0,changePasswordForm,method,submit
URL1=.*?http://localhost:8080/xlWebApp/changePassword\.do.*
URLMatchType1=regex
URLReferrer=http://localhost:8080/xlWebApp/changePassword.do
Context=sbC5iIfJYP05EmLRrbKK+3chgy0c7ByLNn5NiiN8nbbiV0Kd[OIM Web Interface]
AT_AppGUID=87dbf26b-9f09-4838-9d82-1088b31647f1
AuthGrade=1
IDField=0,0,0,text
PassField=0,0,0,password
Section1=dc7bd56d-474c-45de-b0db-cedc5cb35853
Section2=3711a0a2-89a1-47ee-9259-e30512f84515
URL1=.*?http://localhost:8080/xlWebApp.*
URL2=.*?http://localhost:8080/xlWebApp/changePassword\.do.*
URLMatchType1=regex
URLMatchType2=regex
Context=yOujHpJJMmkJ13AZJDejHvWYTKLLyjLnIaRvyzJ3hJklXr88[*Other Webs]
Section1=OIM Web Interface
Context=HjQ1393n8Cgw7C3RPaiQkT6/baBtmFT1j6TwgNrqOQcKUZoXSAVE THE FILE “OIM_WebInterface.file”
_______________________________________________________________________
To define a template for the OIM Design Console:
1. To install the Java Helper Object in the JRE of the OIM Design Console
The JRE is located in OIM_CLIENT_HOME/xlclient/java
Open eSSO Administrative Console and select New -> Windows Application
3. Select Logon and pick the OIM Design Console window
__________________________________________________________________________
[OIM Design Console]
AllowClassName=com.thortech.xl.client.base.dlgLogin
AppPathKey1=java.exe
AppSubType=1
AT_AppGUID=03fc9953-f988-4b6e-a457-078424060dba
AT_PageGUID=2da60d04-fa77-4421-9588-6e3c8ca09672
AT_PageName=OIM Design Console
AuthGrade=1
IDCtrl=1:1:2:1:1:1:6,null,class com.thortech.xl.gui.base.tcTextField,text
MatchType1=exact
OKCtrl=1:1:2:1:1:1:11,null,class com.thortech.xl.gui.base.tcButton,push button
PassKeyCtrl=1:1:2:1:1:1:7,null,class com.thortech.xl.gui.base.tcPasswordField,password text
UseJHO=1
WindowTitle1=Oracle Identity Manager Design Console
Context=vqzf28ldwt288QXPEk30AH1ZTTfH8ICS9f+1HJL3Ym9AVvqK
[*Other Apps]
Section1=OIM Design Console
Context=szg+OZS8oYMoi85lPcEIMY0i/Gc8gpZUpjt2VUoNyvi0ha19
____________________________________________________________________________
Save the file name with “OIM_DesignConsole”
eSSO: Creating An Application Template For MS Outlook
To create the application template, perform the following steps:
1. Administrative Console -> Applications -> New Windows Application
2. Select Logon
3. Select the Outlook logon window from the list
(Module=OUTLOOK.EXE and Window Class=#32770)
When selected, the window border will flash.
4. Select the credentials fields:
ID=101 -> Username/ID
ID=102 -> Password
ID=1 -> OK
5. Click Next and Finish
6. Publish the Outlook application template to the repository
eSSO Integrating With PeopleSoft Web Client
The PeopleSoft web interface login screen is.
Please note that the change password screen can be accessed in two different ways:
1. By using the FastPath -> PSWD
2. By using the menu: My System Options -> Change Password
The goal is to have eSSO respond to the change password page regardless of the link used to access it.
The first step is to define create the template and define the Logon from:
1. Open eSSO Administrative Console
2. Select New-> Web Application
3. Enter the URL of your login screen, for example http://hostname:port/jde/taskexplorer/servlet
4. Detect the credential fields and the submit button
5. Edit the form definition and make sure the URL is set as "Regular Expression", and has the following format:
.*?http://hostname:7080/jde/taskexplorer/servlet.*
To define the form for the change password screen:
6. Select the application template defined before
7. Right click and New Form
8. Navigate to the change password page using the wizard
9. Give a name "PwdChange" to the Form
10. Edit the URL in the form and make sure is set as "Wildcard" and has the following format:
http://hostname:port/jde/servlet*
______________________________________________________
Save the Following Below Content “PeopleSoft_JDE.file”
______________________________________________________
***************************************************************************************
[47f78222-ab13-4b94-8d57-96f8a26b727e]
AT_PageGUID=47f78222-ab13-4b94-8d57-96f8a26b727e
AT_PageName=PeopleSoft
AutoOK=1
IDField=0,F1,User,text
ParentKey1=PeopleSoft
PassField=0,F1,Password,password
SubmitField=0,F1,5,submit
URL1=.*?http://hostname:7080/jde/taskexplorer/servlet.*
URLMatchType1=regex
URLReferrer=http://10.166.234.184:7080/jde/taskexplorer/servlet
Context=joXfPQn1rxy9e+K8fogo2Mdeon6VF/FScEnrUP+4Q/0nZvoX
[9f3d9060-e9b8-4938-b6ad-3cbda97f20bb]
AT_PageGUID=9f3d9060-e9b8-4938-b6ad-3cbda97f20bb
AT_PageName=PwdChange
AutoOK=1
NewPWField=4,P98OWSEC_W98OWSECD,0_15,password
NewPWField2=4,P98OWSEC_W98OWSECD,0_17,password
ParentKey1=PeopleSoft
PassField=4,P98OWSEC_W98OWSECD,0_8,password
SubmitField=4,P98OWSEC_W98OWSECD,2,anchor
URL1=http://hostname:7080/jde/servlet*
URLMatchType1=wild
URLReferrer=http://10.166.234.184:7080/jde/taskexplorer/servlet
Context=LfeYXg21Sn44ScTai/SlSRtJfuWygp7OYg8jbqaPMUf6Oj2c
[PeopleSoft]
ActiveLogon=1
AT_AppGUID=ba08b75d-c249-4d92-965c-4be57aa9a4db
AuthGrade=1
AutoOK=1
IDField=0,0,0,text
PassField=0,0,0,password
Section1=47f78222-ab13-4b94-8d57-96f8a26b727e
Section2=9f3d9060-e9b8-4938-b6ad-3cbda97f20bb
URL1=.*?http://hostname:7080/jde/taskexplorer/servlet.*
URL2=http://hostname:7080/jde/servlet*
URLMatchType1=regex
URLMatchType2=wild
Context=eo7C7PuZ2BSsO70jbIcxUSbbdQq/eA54hMyxzf6dbWTA2zhz
[*Other Webs]
Section1=PeopleSoft
Context=pSOeSg2GRGCFmETssLVs3D52ywZ2vvnWVeNkB19vCRUCIOTl
****************************************************************************************
Esso Will Not Auto Login To Peoplesoft HR
Condition as below
Using Logon manager, customer configured ESSO to auto log in to Peoplesoft HR (Word document attached). After customer closes Logon Manager and Peopletools, customer re-opened Peopletools and the logon screen just sits there. Nothing happens.
Follow next steps:
1. Open eSSO Administrative Console and select Applications -> New Windows App
2. In Add Application screen, enter a name for the application (for example ‘Test1’) and select 'Windows' for application type.
In Application field the selection should be 'New Windows Application'.
3. In Form Wizard screen select 'Logon'
4. At this point a list of all opened windows on your session will be displayed. One
should select your “Peopletools version 7.62” Once selected the windows will start to blink.
Click 'Next'.
5. In the Credential Fields window you should check "Use 'Send Keys' for this
form, do not use Control ID's" at the bottom.
6. Click 'Next' and then 'Finish'.
7. Select the 'Fields' tab from the top of the window and on the tab select
"Send Keys" as transfer method and click 'Edit'.
8. In 'Send Keys' window you have "Current Actions" in the left and "New
Actions" in the right of the screen.
+ Select 'Username/ID' from 'Field Type' and 'Enter' as 'Character to insert
after field' then click 'Insert'
+ Next select a Delay from the list in the left. Set 1 second for "Length of
delay" and click 'Insert'.
+ Select 'Fields' again and Password and click 'Insert'.
+ Next select a Delay from the list in the left. Set 1 second for "Length of
delay" and click 'Insert'.
After this the list in 'Current Actions' should be like this:
Username/ID
[Enter]
[Delay: 1 s]
Password
[Enter]
[Delay: 1 s]
19. Click 'Ok' and save your application.
10. Now the new defined application can be exported to the Agent. At this point
the application is ready to use.